Gone are the days when you needed a developer to build an app for a relatively easy task. No-code and low-code development let you dramatically increase the speed of building and bringing simple (and, sometimes, not-so-simple) apps to market. I swear, half my life is being run by Zapier at the moment: Book a meeting with me, and all sorts of things happen automatically in the background to ensure that our meeting is on the right calendars, is transcribed, and the video of the call is stored away and tagged with your company’s name.
The ease of creating apps that low-code and no-code offer has trade-offs, though: In order to work, they need access to some pretty sensitive data. If someone wants access to my data, they could try to hack my email, or they could hack one of the many automations tied to my email accounts. When more and more apps are essentially running on the same underlying architecture and code, they become a very tempting target for hackers and others with nefarious intentions.
Enter Nokod Security, which offers to monitor no-code and low-code apps for security vulnerabilities and mitigate breaches.
The company recently raised $8 million from Acrew Capital, Meron Capital and Flint Capital, and the team was gracious enough to share the (lightly edited) deck they used so we could take a sneaky peek under the hood.
We’re looking for more unique pitch decks to tear down, so if you want to submit your own, here’s how you can do that.
Slides in this deck
The company has left the 21-slide deck intact except for a few parts.
- Cover slide
- Team slide
- Example no-code apps
- “Who uses no-code apps”
- Macro trend: The Low-Code / No Code trend
- Threats and attacks slide
- Problem slide
- Threats and Attacks slide
- Attack vectors slide
- Mission slide
- Solution slide
- Architecture slide
- TAM slide 1
- TAM slide 2
- TAM slide 3
- Go-to-market slide
- Competition slide
- Validation slide
- (Redacted) Validation takeaways slide
- Timeline slide
- Contact slide
Three things to love
Nokod’s deck has a lot of cool things going on, as well as some stuff that had me pretty confused. As always, I’ll get to my misgivings and OldManYellsAtCloud.gif feedback in just a moment. For now, let’s look at the slides that got me excited.
Give me a T! Give me an E!
Okay, I’m not gonna spell out T-E-A-M in the subhead, but this is an example of a company that knows its strengths. In an early-stage company, a founding team that has an unfair advantage is a straight-up superpower. Nokod has all bases covered on that front:
[Slide 2] Extraordinary founding team. Image Credits: Nokod
The two co-founders have both started and exited companies in the cybersecurity space before. That’s a hell of a way to catch an investor’s attention. Relevant experience and successful exits screams “unfair advantage.” Even after just reading this one slide, I was pretty unsurpised that this company successfully raised money.
Apart from the obvious, this slide shows that the founding team understands what’s important in a pitch deck: If you’ve got incredible traction, lead with that. If you don’t, highlight your experienced team.
Well-articulated problem
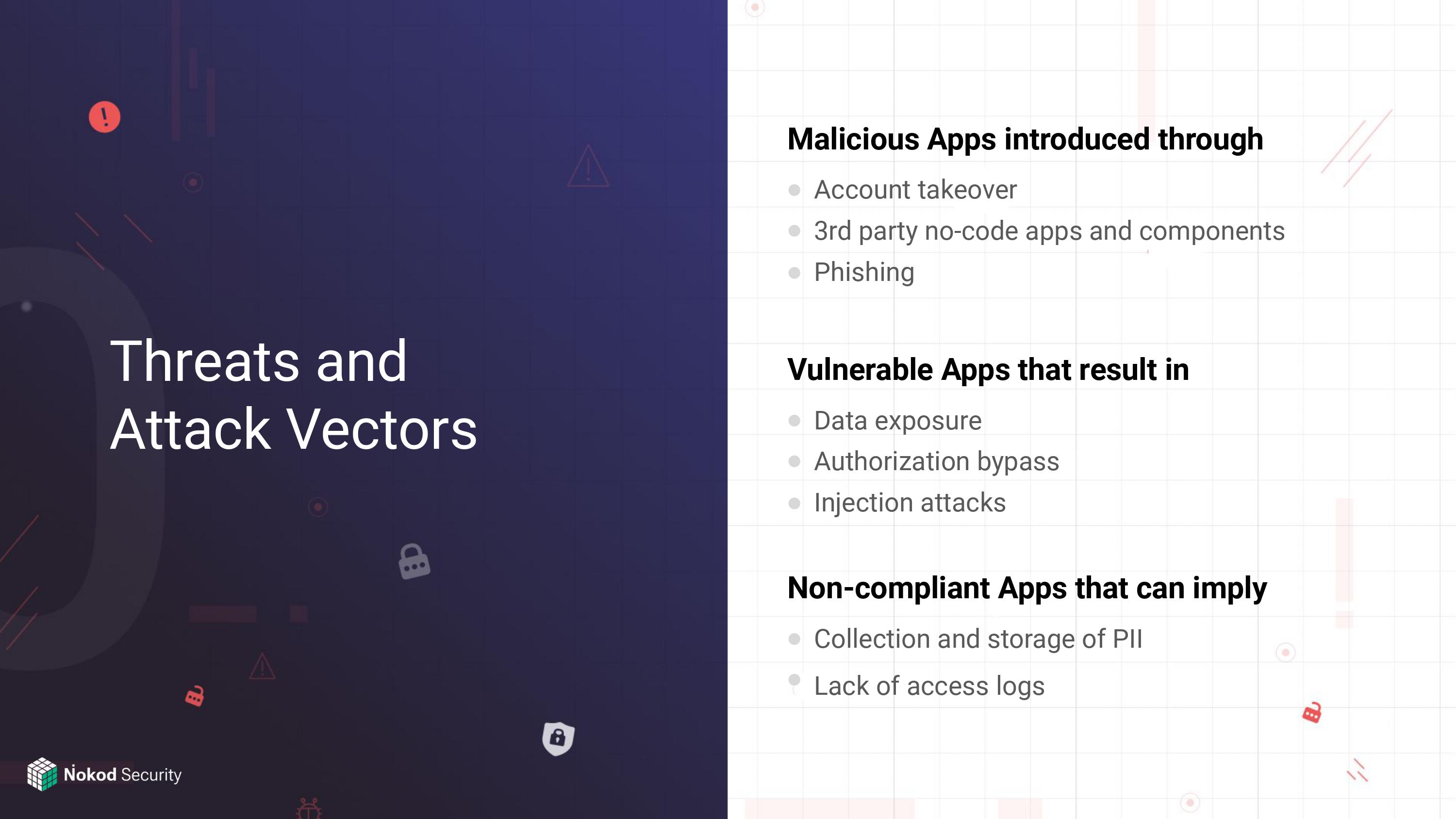
[Slide 9] An elegant outline of the problem at hand. Image Credits: Nokod.
A good fundraising story will have a good explanation of what the problem is and why it might be worth solving. Not everything on this list is well explained. To wit: Do you, without googling, know what PII is, or, indeed, why collection and storage of PII might be a bad thing?
The company could have taken the effort to explain the impact of some of these issues and why low- and no-code apps are particularly vulnerable in these situations, but I get the message in broad strokes: The cost of embracing no-code and low-code is that people might not always know exactly what’s going on, and if something does happen, it can be hard to figure out exactly where the ne’er-do-wells gained entry to a system.
A better go-to-market slide than most

[Slide 16] Let’s sell this thing. Image Credits: Nokod
This go-to-market slide has a clear profile of the customer: how they can be reached, what the business model is, and where they are geographically.
Building a coherent go-to-market strategy can be surprisingly hard. It’s what I end up arguing about with my pitch coaching clients most often. Having some vague, hand-wavy “build it and they will come” theory works when you are focusing on the product, but if you are raising money to acquire customers, you don’t get to shrug and say, “We will figure it out when we get there.” You aren’t getting there. You are raising money to execute, so you are there.
This go-to-market slide has a clear profile of the customer: how they can be reached, what the business model is, where they are geographically, and even who the decision-maker is within the business. I’m not sure how many medium-sized companies have a CISO or director of application security. I suspect a lot of the time, these decisions fall to a CTO rather than a dedicated, clearly defined security role.
Still, as an investor, I can look at this and see the outline of a plan. My next question would be: “Okay, talk me through your process. How do you actually land a sale?” The story should be consistent and outline a good sales funnel — something like, “The leads come from X, we reach the decision maker through A, B, and C, and then we close the deal 25% of the time. But we suspect we can increase that percentage if we do Y and Z.” An answer like that will pass muster for me, and doubly so if the company already has paying customers and can point to the sales process it used.
In the rest of this teardown, we’ll take a look at three things Nokod could have improved or done differently, along with its full pitch deck!


